“Phishing” is when scammers send you an email that’s trying to trick you into revealing information, or installing malware on your computer or phone. And a lot of you are falling for it.
How do I know?

Hundreds of thousands of people have “interacted” with me by email, from friends I chat with on an almost daily basis to people who subscribed to my newsletter and got at least one message from “me” (aka, my email address). I get to know a lot of readers by name because they comment, or simply because they have recurring subscriptions and I see their renewals come in.
For weeks I’ve been getting a lot of very similar emails, and I often recognize the “From” name — various readers. They are always in my spam folder.
Yes, I recognize “Mary Wilson” as a reader, and chose that example because not only do I have at least two readers named “Mary Wilson”, but it’s a generic-enough name to not embarrass them. Many others come from much more unusual names that I also recognize as readers.
This particular flavor of scam all have the same format: a URL to click that looks like but isn’t a link to search for my email address on Google. That’s called a cloaked link.
What is it cloaking? Malware. Click the link and you won’t go to Google, you’ll go to the criminals’ site.
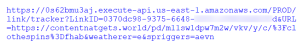
In fact, the link is double-cloaked: it first goes to the link-shortener and -tracker Bit.ly, as shown above. From there Bit.ly sends it off to a redirector hosted on Amazon Web Services which, no, doesn’t have the malware, because it then hops over to the real destination, contentnatgets.world, a 27-day old (as of today) site hosted on the “Google Private Cloud” at an I.P. address assigned to Finland in South Karelia, very close to the Russian border.
Smell a rat yet?
And see all that LinkID coding in there (some of which I blurred)? That lets the criminals know exactly who clicked their link: they have now verified that 1) your email address works, 2) you opened the message, and 3) you are gullible enough to have clicked the link — the perfect mark for further exploitation.
But what’s the harm?
First, once you get their malware loaded up, it scans your email and address books looking for new victims: your friends, business associates, charitable organizations, etc. will start getting similar emails with your name in the From line. I get many of them daily since my address is in so many of your email folders.
Second, what else is in your email? Messages from your bank(s), investment companies, retirement funds, and more. And maybe the malware you loaded has a module to grab your login and password for those financial institutions and send that to them. I mean, why wouldn’t it? They’re criminals and they’re after money. Your money. Easy money.
Getting scared yet? You should be!
Lesson Number 1
Never ever ever click an unsolicited link.
The message is “from” a friend? Check it: is that their real email? Does the link even go where you think it does? Hover it with your mouse, rather than clicking it, as shown above, to see. (The procedure is different on phones and tablets: learn it!)
Note that on most browsers that preview comes up in the lower-left corner of the window, just as shown above, and could be far enough away from the link that you don’t notice it.
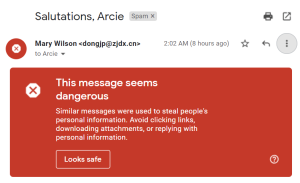
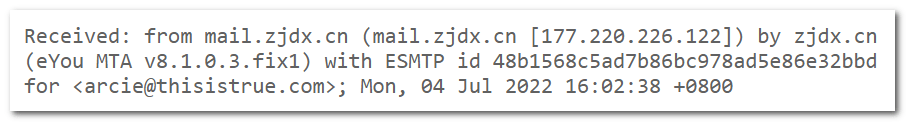
So, am I sure these are Russian criminals? Nope: could be Chinese. Why Chinese? Because “Mary Wilson’s” email address is shows as dongjp@zjdx.cn and, indeed, here’s the header of where the message was sent from:
But then, within 24 hours of this one, there was another from “Mary Wilson” …from a different email address. Routed through different servers. The criminals could actually be anywhere: this is the Internet, after all! Anyone can rent a server anywhere.
The “Google search link” in that message also cloaked a (different) Bit.ly URL, which went similarly through different routes to a different but similar final destination (naturalgetcontents.world), which is also 27 days old. To me, the same fingerprints = the same criminals.
Can You Complain?
Sure, have at it. First, you need to find the abuse form at Bit.ly, and know what to tell them so they can take the needed action. And then the abuse form at Amazon Web Services (ditto). And Google Private Cloud (ditto). Maybe the registrar of the .world domains (ditto).
But, of course, the criminals will simply set up a different Bit.ly address, copy their code over to new AWS and GPC instances, and start again.
Which is what they are already doing, as noted above, because someone might go to the trouble and get one of their paths shut down, so they are simply proactive and copy their efforts multiple times with different routes to get the same information, and the victims are left playing whack-a-mole while the criminals clean out bank accounts to fund yet another round of scamming.
I sure don’t have time for that. Unlike criminals, I need to work for a living.
So What, Then?
So get smarter: don’t click the frigging link!
And do this: scan your computer for malware. My favorite tool for this is Malwarebytes, but even there you need to be smart: get their free scanner, install it or other options carefully to not get anything you don’t want (like toolbars, or a free trial of paid services). You might want the paid services, but make that decision consciously, not letting them default you into paying. And certainly don’t start with paying: test first.
Once the scan is complete and shows you clear (or shows you need to remove malware and then scan again), change your passwords on all important sites, such as your financial institutions. Every password needs to be unique (never use it on multiple sites), long (long is more secure than complex), and kept in a safe place.
What safe place? I use the free Bitwarden password locker. I only have to know one password: the one that opens Bitwarden to decrypt my passwords and fill them in for me. Yes, it’s safe, and is highly recommended by experts that are much more knowledgeable than I am about computer security (and I’m no slouch at it).
Last, if any of this is new or surprising to you, you simply must read my free Spam Primer, which covers other types of noxious, criminal email practices. On its own site, SpamPrimer.com (not a cloaked link!)
The bottom line is what True is about in the first place: Thinking. That’s why so many people subscribe, and you should too if you don’t already. [Open Subscribe Form] It could save your retirement accounts, just as a start!
– – –
Bad link? Broken image? Other problem on this page? Use the Help button lower right, and thanks.
This page is an example of my style of “Thought-Provoking Entertainment”. This is True is an email newsletter that uses “weird news” as a vehicle to explore the human condition in an entertaining way. If that sounds good, click here to open a subscribe form.
To really support This is True, you’re invited to sign up for a subscription to the much-expanded “Premium” edition:
Q: Why would I want to pay more than the minimum rate?
A: To support the publication to help it thrive and stay online: this kind of support means less future need for price increases (and smaller increases when they do happen), which enables more people to upgrade. This option was requested by existing Premium subscribers.

Also, for e-mails that don’t necessarily have links that seem a little off, but show “from” your contact’s address, see if there is a different reply-to address. The scammer may send an innocuous message getting you to reply to the wrong address.
—
Good extra detail. -rc
I have been into email etc since 1974 (local network) now everywhere. Malwarebytes is what I put on everyone’s computer/tablet. It works as long as it’s up to date.
—
Every time you run it, it checks for updates. DO let it update before scans. -rc
Google also has an ‘orange’ warning about phishing if it’s a new email from someone who is on your contact list. It’s only happened once to me, with a friend who sent a message using her professional email for the first time. I did check with her by phone before opening it.
I forward all of the suspected phishing messages I get to:
phishing-report@us-cert.gov
—
While I have no idea how effective that is, at least “they” are monitoring the situation, and probably acting against the bigger players. -rc
If you are in Canada, there’s also this govt anti spam program:
https://www.fightspam.gc.ca/eic/site/030.nsf/frm-eng/MMCN-9EZV6S
Caveat: have not kept up with it bc GMail doing fine job filtering from even hitting inbox (actually spam folder).
HTH someone.
Some sickening sods out there! Thanks for the info.
Cyber Security departments make employees take lessons on how to detect and avoid email scams. Frequently, they tell you in these classes not to click on embedded links. In the demand you take this class email is an embedded link and a reply-to different than the sender.
Odd that for the last 30 years of my complaining about this, they have yet to change. Worse is that these classes are typically outsourced making the email seriously in violation of corporate standards.
—
Smack my forehead! -rc
I get forwarded emails from several charities I help lead. A favorite ploy is to say I have emails blocked and I need to verify the (president@, or treasurer@) using my login and password to receive them. When I ask the host, they are invariably phish. I also get emergency emails from “the president” to send money to someone. Sadly, too many people must fall for these, since they continue.
—
I get such emails too, from the “mail administrator” of my domain, almost always from a foreign address. Funny, I’m my own mail administrator, and don’t live overseas. -rc
“The message is “from” a friend? Check it: is that their real email? Does the link even go where you think it does? Hover it with your mouse, rather than clicking it, as shown above, to see. (The procedure is different on phones and tablets: learn it!)”
For those who want/need to know, on iOS, you use a “long press” to uncover the actual address. Press on the link as if to go to it, but hold your finger in place for about two seconds and it will pop up a menu with additional options that also includes the actual URI the link goes to. That menu is also how you can copy the link if you wish to report it to some agency.
Android is probably different, and I do not know its method as I do not use Android much.
—
It is, at least in Gmail on Android, but it’s possible it’s different in different apps. (Hopefully it IS the same, but I don’t know for sure.) -rc
Android here. It is the same on the mail app (not gmail, just the general one). Also everywhere else, such as websites: long press on the link to get the pop up menu.
To add what Susan in Virginia said: pay attention to the “From” address, especially if you, like me, want to let our friends know they have been hacked — or to verify that you know the person who sent the e-mail: really pay attention to the name. Let’s say Joe Rum allegedly sent the e-mail. Did it come from joe.rum@… or joe.rurn@…?
Notice in the first example, Rum is spelled correctly; in the second, it is misspelled.
Two things:
1) Set up two-factor authentication (2FA) on as many accounts as possible, especially your financial accounts. It’s preferable to use an authenticator app, but text also works (although is less secure).
2) I used to be in charge of the team that sent out all of the non-marketing emails and texts for one of the largest banks in the country. We VERY rarely would ask you to click on a link in an email, and when there was a link, I complained loudly to my business partner that it was a bad idea. However, the emails go through many reviews, and if they have any mistakes, bad grammar, bad formatting, etc., I can guarantee that it’s a fake. Bottom line: if you get an email from any of your financial institutions, don’t click on any links. Instead, go to your browser and go to their website directly.
—
I concur with both points. -rc
I once received an email on my work account, apparently from a Data Security company, inviting me to click on an embedded link. It looked very odd so instead I reported it to the Administration Manager. It turned out is was a test, set up by the firm’s IT support company. I passed!
As someone in ‘Corporate America’ we are subject to annual training, in addition to random testing that you should report as phishing using provided tools. Reading this I realize others are not so lucky.
I worry about my elderly parents and try to educate them frequently about this type of scam. This will be shared with them as well.
It is also a good idea to use unique email addresses for each business that you deal with. Some of the forged emails are very good. If you don’t have your own domain, you can use the comment field in the email address. Some web sites are broken and don’t honor it, but it is USER+COMMENT@DOMAIN, where “+” is the actual “+” character. So an example would be “fred+mybank@mydomain”. This helps to detect forged email since if you get an email not to this address from your bank, likely it isn’t from your bank.
In addition, if you get spam then you can look at the to address and see the source of it. I received spam to an address only given to a credit card company, which indicates that the information was compromised. In another case the email on a list was compromised so I knew the source of it. Others on the list likely got the same spam, but they didn’t know who to complain to. Oh, never clink on links even if you are 100% sure of where it came from as their account could have been compromised or they might not really be trusted.
—
I only apply the last point to financial and other “important” sites. If Bank Inc. wants me to check on a transaction, I don’t click on the link, I log in to Bank Inc. from my own bookmark. Looking at the domain is not enough, since it is often something like wellsfargo.com.somescammersite.ru, or even like wellsfango.com, which ain’t it either. -rc
The example is even more fun because it suggests that the spam message came from China based on the (spammer-supplied) dns domain, while the IP address is actually assigned to Brazil. That message actually did come from everywhere.
—
They go to a lot of work to obscure their tracks. Just imagine if they put that much effort into honest work?! Improve the world instead of screw it up more? Radical! -rc
I stopped using Malwarebytes because the updates always failed — hanging at about 90% and leaving me with no option but to restart my computer. Out of curiosity, I started an update just before going away for the weekend. 48 hours later, the update was still showing about 90%… I now use a combination of AVG, CCleaner and common sense.
—
Common sense does go a long way, which would be great it most people had it. I’d be suspicious that a failed update was an indication that malware was blocking that update, so it was smart to switch to something else to check your system rather than just shrug. -rc
I used Norton for about ten years, but stopped after two different sets of update disks (3-1/2 floppies, about 20 each). The update failed and locked my system both times. The second set came directly from Norton. I finally used another program after I reformatted the HD.
—
Alas, IMO Norton went downhill after Peter Norton sold the company. -rc
I check the return email address for businesses and NEVER use their link to check their information on my account. Some are so lazy, the return address does not even match what its supposed to. Most big businesses have their name in their e-mail. I am sure they will learn and start faking that part too, but for now just simply making sure the return e-mail has the business name is an easy first step. If it does have the right name, then I still go to the main website and check to see if everything is okay. I don’t use the link in the e-mail.
I don’t know if this is true with modern Outlook and/or other email clients or not (I still use Outlook 2007), but my Outlook has an option to always read all emails in plain text only.
Email is almost exclusively a plain text medium (which is the way it was originally designed), and using HTML in emails is rarely if ever actually needed (except for in rare circumstances such as This Is True subscriptions, etc).
All the email I send is in plain text, and all email I receive is read as plain text only. That way I can SEE exactly where each link is going. If it looks legitimate, then with a click of a button I can ask Outlook to display it in HTML (and even then, for security, it won’t show you the images without you specifically asking it to do so).
There’s no legitimate need to use HTML except for things like This Is True, etc.
For 99.7%+ of normal everyday email (especially casual emails from friends, etc) should be sent in PLAIN TEXT. There’s no real need for HTML.
—
HTML allows for nicer formatting. TRUE is written with bold slugs and italic tags, and I like that I can show it that way in the emails, but sent it in plain text for 999 weeks. -rc
Oh, I really like having TRUE in HTML, Randy! I’m glad you switched TRUE to HTML! I wouldn’t want it any other way!
I’m just saying that for almost all OTHER emails, plain text is the way to go. RARELY during casual conversational email between friends does one find the need to use bold or italic or bullets or a different font, etc.
My point is, the type of phishing scam vulnerability you described can only occur (or is MUCH more likely to occur) when HTML email is used, so in order to reduce your exposure to such vulnerabilities, one should refrain from using HTML emails. Use plain text. It’s less risky. Use HTML only for things that MUST be in HTML. Like TRUE. 🙂
—
Oh, I understood you. I was just filling out the details, as you continued here. I was not feeling challenged or offended. 🙂 -rc
I have a hard time trusting any one of only a handful of companies with all my passwords. What’s to keep them from suddenly charging their clients $1000 to access their passwords, in effect, the password managers becoming ransomware-ers themselves.
And how do you keep PMs updated across multiple devices without relying on the insecure cloud?
Lastly, more companies have been the source of breaches than individuals have.
I just hate having to be in a state of hyper-vigilence everywhere, all the time online It’s nerve-wracking, and frankly, beyond this fogey’s skill set.
—
So you think maybe the vault companies would commit fraud just in case they might get a couple of million bucks? You’re not thinking that through. Next, they can’t see your passwords: they’re encrypted using the passphrase only you know. (Lose it and you’ll never get your passwords back.) The vault moves from device to device as updated, and never having been decrypted. Last, if you’re smart you periodically export your password vault and print it, and put it in a safe deposit box and/or fire safe. If you’re not smart, well, you don’t do any of this, and take your chances, because a LOT more individuals lose accounts (or worse, the money in those accounts) than you think. -rc